In my copious amounts of free time, I have been poking around at a few different home Network Access Devices (NAS). These are an attractive target because of the extensive attack surface and also, the software in the home versions is the same as the enterprise class systems. These devices tend to sit in a privileged area in a network as a central repository for the home offering services well beyond the classic NAS offerings including serving music, images, video, monitoring surveillance camera, connecting to the cloud, etc…
In this report, I was digging into a Synology DiskStation 216+II running firmware version 6.1-15047. This is an older version of the OS as these findings are almost a year old and while fixed for some time, this posting (and others pending) is way overdue because I have just been too busy.
On to the findings!
Vulnerability #1 CVE-2017-12076 and CVE-2017-12077
This vulnerability impacted two operating systems, the Synology Router Manager (SRM) and the DiskStation Manager (DSM).
Denial of Service
The device provides functionality to also act as a router with firewall and port forwarding capabilities; as I said, these are not just simple NAS devices.
The Synology EZ-Internet application was subject to a DoS attack; by sending a relatively small number of port forwarding rules, about 1,000. It would cause the device to stop responding and required a hard reboot after 30 minutes of waiting. This attack required privileges on the system. I found this one when fuzzing the interface parameters looking for other vulnerabilities and noticed it would lock up the web interface of the system.
Vulnerability #2 CVE-2017-12074
Path Traversal and File Write
There is an interesting path traversal issue with an ability to create or overwrite files. By modifying a Create Master Zone message, it is possible to overwrite files in the NAS that have the same permissions as the Master Zone process or create new files.
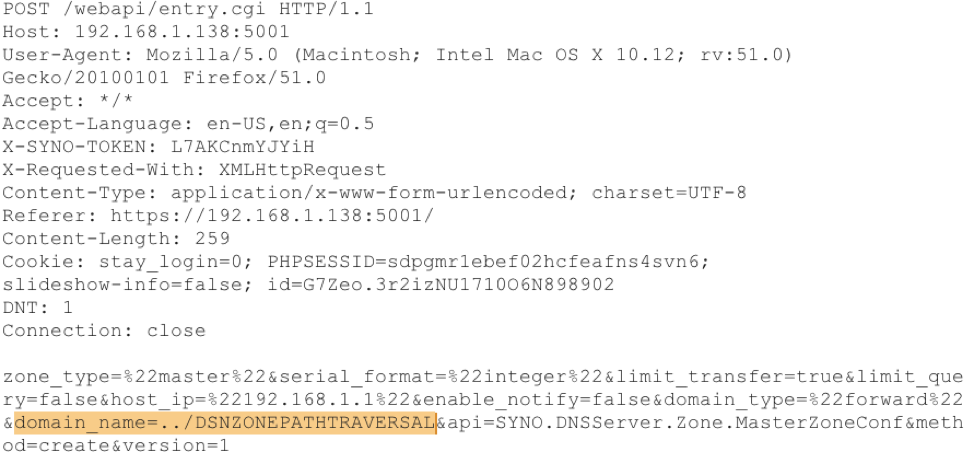 This captured and modified message in Burp, shows the parameter (domain_name) and one possible modification (../DNSZONETRAVERSAL) that can be used to execute the path traversal and create files in various locations on the system.
This captured and modified message in Burp, shows the parameter (domain_name) and one possible modification (../DNSZONETRAVERSAL) that can be used to execute the path traversal and create files in various locations on the system.
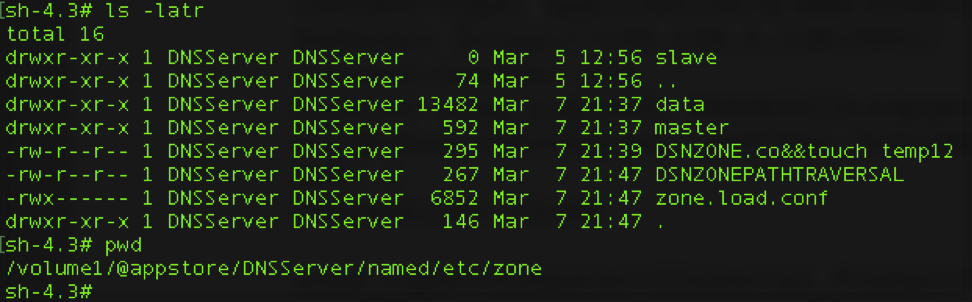
Below is a screen capture of the results showing the creation of the file “DNSZONEPATHTRAVERSAL” outside of the data directory where it should be held. As you can see from some of the other files, I was playing with this to see if I could exploit it in other ways.
This attack required admin privileges on the system.
Vulnerability #3 CVE-2017-9555
Reflected XSS
The NAS provides some wonderful photo management, sharing and editing software. I was able to find a reflected XSS attack. By modifying the image parameter, an attacker is able to trigger a reflected XSS attack.
This is an example of such a string which will result in the classic XSS alert popup box: https://IPADDRESS/photo/PixlrEditorHandler.php?action=notify&image=q%27-alert(1)-%27q
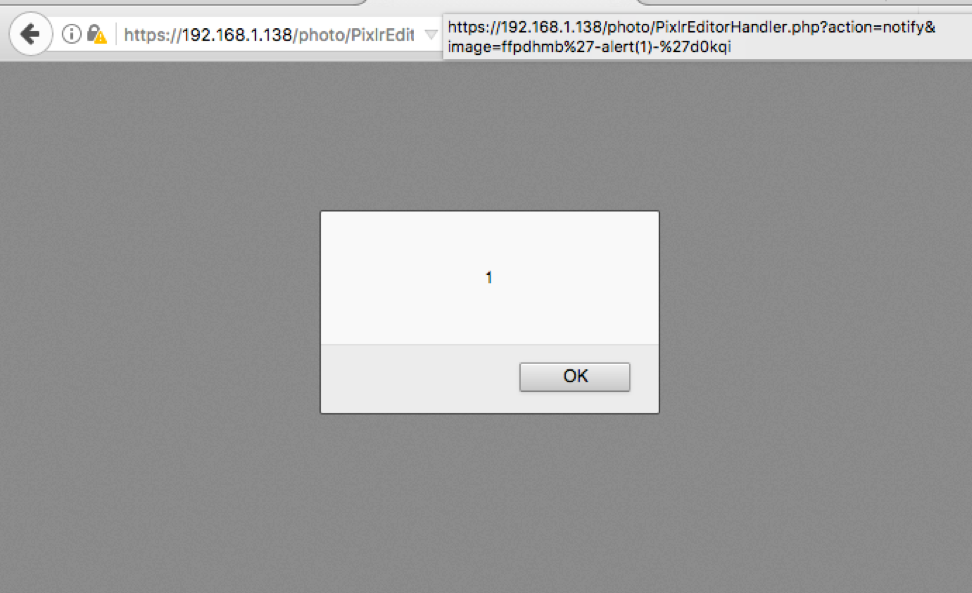
This type of reflected XSS is very valuable as an initial vector when trying to chain attacks together for an exploit. This vulnerability could allow an attack to manipulate users logged into the photo management system but not the admin’s web interface. The photo station software was on a different port from the web admin interfaces and Cross Origin Resource Sharing (CORS) protections in the browser prevented me from utilizing it as an attack vector against web admin’s session.
Working with Synology
When I reported these issues, Synology responded to my report in under 24 hours that they were able to reproduce most of my findings, following up shortly that they reproduced the remaining. Their responses were very quick, timely and were a pleasure to work with. The delay in reporting the information is my fault.
Disclaimer
This research was conducted on my own time, on my personally owned hardware and is in no way connected with my employer.
